Is Pam Hardy Still Alive? Exploring The Enduring Strength Of Privileged Access Management (PAM)
So, you might be wondering, "is Pam Hardy still alive?" It's a question that, in a way, often pops up in various forms, especially when we talk about things that are truly vital and foundational. While there isn't a person named Pam Hardy that our cybersecurity discussions usually center on, this very question gives us a pretty good chance to talk about something incredibly important that shares a similar name: Privileged Access Management, or PAM. This essential part of keeping digital spaces safe is, actually, very much alive and thriving.
You see, the idea behind asking if something is "still alive" often comes from a place of wanting to know if it's relevant, if it's effective, or if it's keeping up with the rapid changes around it. For Privileged Access Management, that question is rather fitting. In a world where digital threats are constantly changing, knowing that your core defenses are not just present but also evolving is truly important. This piece will look into why PAM remains a cornerstone of strong security.
We're going to explore what Privileged Access Management really is, how it works to protect sensitive information, and why it's more crucial than ever in today's digital landscape. It's about making sure that the tools and strategies designed to keep our data safe are not just active, but robust and ready for whatever comes next. So, let's get into the details of this vital security approach.
Table of Contents
- What is Privileged Access Management (PAM)?
- Key Facts About Privileged Access Management (PAM)
- How PAM Works: Safeguarding Your Digital Assets
- Why PAM is More Vital Than Ever
- PAM in Action: Real-World Impact
- The Future of PAM: Staying Ahead
- Frequently Asked Questions About PAM
- Conclusion: PAM is Very Much Alive
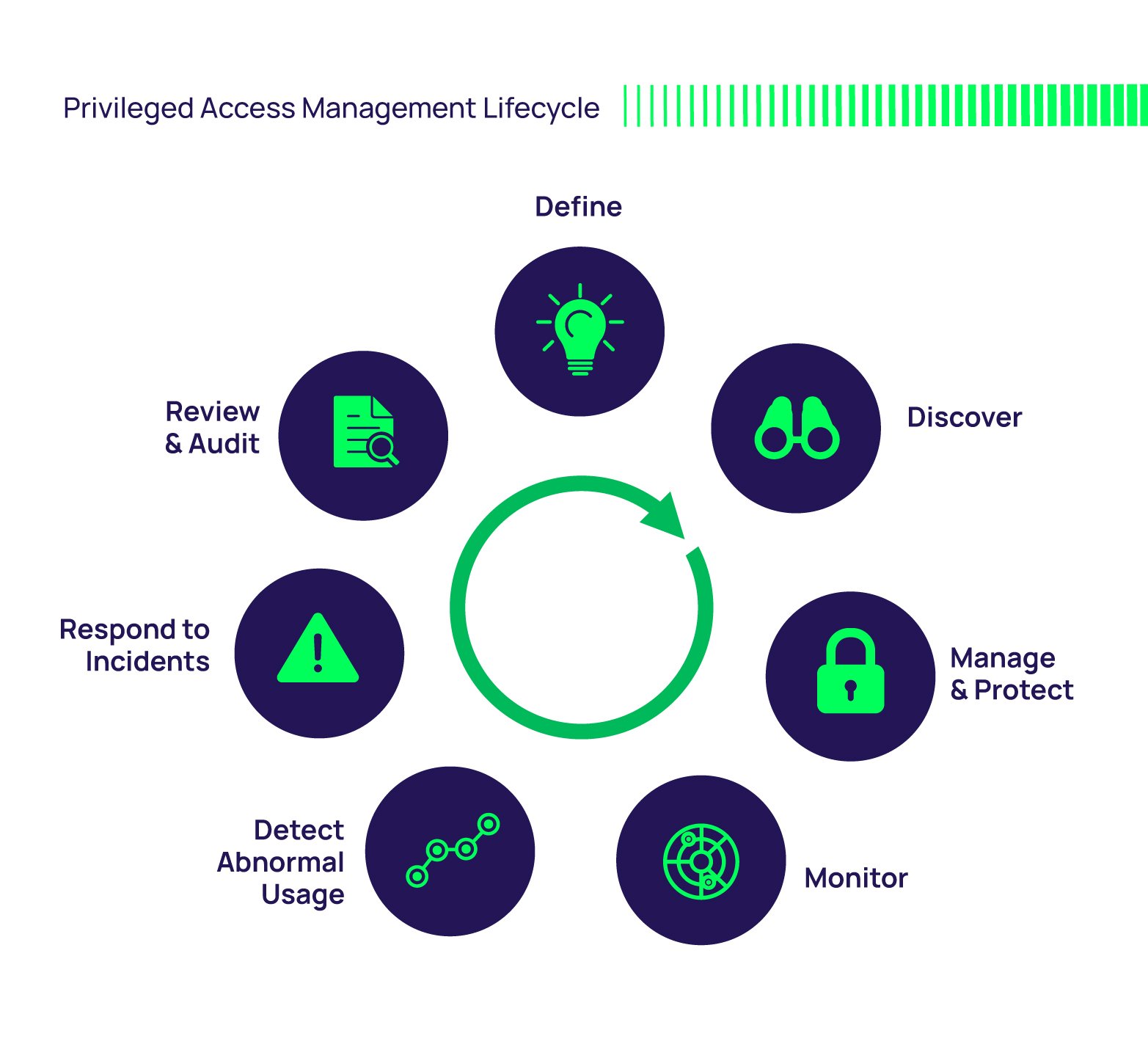
What is Privileged Access Management (PAM)?
Privileged Access Management, or PAM, is a type of identity security solution that helps protect organizations from cyber threats. It does this by watching, finding, and stopping unauthorized actions. Basically, it's about controlling who gets special access to important systems and data. Think of it like the ultimate gatekeeper for your most sensitive digital areas. It's a core part of how businesses keep their information safe and sound.
In simple terms, PAM is a cybersecurity plan and a collection of technologies. Its main goal is to protect an organization's most sensitive data and critical systems. It does this by carefully controlling and monitoring who can get into these areas. This means that only the right people, with the right reasons, can access the most important parts of a network. It's a system built on the idea of "least privilege," meaning people only get the access they absolutely need to do their jobs.
PAM is also a branch of cybersecurity that focuses on the control, monitoring, and protection of privileged accounts. These are accounts with special powers, like those used by system administrators, IT staff, or even automated processes. These accounts can change settings, access sensitive data, or even shut down systems. Because of their immense power, they are often targets for attackers. PAM makes sure these powerful accounts are always under strict watch.
A solution like Mim Privileged Access Management (PAM) helps organizations limit privileged access within an existing and separate Active Directory environment. This means it can work with systems already in place, making it easier to implement without completely overhauling an entire IT setup. It's about adding a layer of security where it's most needed, without causing major disruptions to daily operations. This adaptability is part of why PAM is so widely used.
Privileged Access Management identifies the people, processes, and technology that need privileged access. Then, it sets up specific rules to keep sensitive resources in an organization secure. It's not just about stopping bad actors; it's also about making sure that legitimate users follow safe practices. This includes things like strong passwords, multi-factor authentication, and session monitoring. It's a comprehensive approach to managing powerful digital keys.
Key Facts About Privileged Access Management (PAM)
| Aspect | Description |
|---|---|
| Core Purpose | Protects organizations from cyber threats by managing and securing powerful user accounts and access. |
| Primary Function | Monitors, detects, and prevents unauthorized access to critical systems and sensitive data. |
| Key Components | Combines people, processes, and technology to enforce strict controls on access. |
| Focus Area | Concentrates on "privileged" accounts, which have elevated permissions beyond regular users. |
| Benefit | Safeguards critical assets, reduces the risk of data breaches, and helps meet compliance requirements. |
| How it Works | Enforces policies, monitors sessions, and manages credentials for privileged users. |
| Identity Security | A fundamental part of overall identity management and cybersecurity strategies. |
| Adaptability | Can work within existing IT environments, like isolated Active Directory setups. |
How PAM Works: Safeguarding Your Digital Assets
PAM operates through a combination of people, processes, and technology. This setup lets organizations protect their important assets by making sure there are strict rules about who can get into privileged areas. It's not just a piece of software; it's a whole system that involves how people behave, what steps they follow, and the tools they use. This layered approach is why it's so effective.
One way PAM works is by enforcing the principle of "least privilege." This means that users, even those with administrative roles, are only given the minimum level of access needed to do their jobs. For instance, an IT administrator might need access to a server for maintenance, but not to sensitive customer data. PAM makes sure these boundaries are clear and enforced, reducing the chance of accidental or malicious misuse of power. It's a bit like giving someone only the keys they need for one specific door, rather than a master key to the whole building.
PAM also includes strong password management. Instead of administrators knowing and using the actual passwords for privileged accounts, PAM systems can automatically manage and rotate these credentials. When an administrator needs to access a system, PAM can provide a temporary, unique password or even connect them directly without revealing the password itself. This dramatically cuts down on the risk of passwords being stolen or misused. This is, in fact, a really big deal for security.
Another crucial part of how PAM works is session monitoring and recording. When someone uses a privileged account, PAM can watch and even record their entire session. This means every command they type, every file they access, and every change they make can be logged and reviewed. If something goes wrong, or if there's an audit, this detailed record is incredibly valuable. It provides a clear trail of activity, which is very helpful for accountability and investigation.
Privileged Access Management also focuses on the control, monitoring, and protection of privileged accounts within an organization. This means it doesn't just manage human users; it also manages service accounts, application accounts, and other non-human entities that might have elevated permissions. These non-human accounts are often overlooked but can be just as dangerous if compromised. PAM ensures that all these powerful accounts, regardless of who or what uses them, are secured and managed properly.
Why PAM is More Vital Than Ever
In today's interconnected world, cyber threats are growing in both number and cleverness. Because of this, Privileged Access Management is not just a good idea; it's practically a necessity. Organizations are facing more sophisticated attacks, and many of these attacks aim directly at privileged accounts because they offer the quickest path to a system's most valuable assets. If an attacker gets hold of a privileged account, they can cause a lot of damage very quickly.
The rise of cloud computing and remote work has also made PAM even more important. Data and systems are no longer just sitting inside a secure office building. They are spread across various cloud services, and employees are accessing them from all sorts of locations. This expanded attack surface means there are more entry points for potential attackers. PAM helps extend security controls beyond the traditional network perimeter, making sure that privileged access is secure no matter where it originates.
Regulatory compliance is another big driver for PAM's continued importance. Many industry regulations and data privacy laws, like GDPR, HIPAA, and PCI DSS, require organizations to have strict controls over access to sensitive data. PAM provides the tools and processes needed to meet these requirements, helping businesses avoid hefty fines and reputational damage. It's not just about preventing breaches; it's also about proving that you're doing everything you can to protect information.
Furthermore, insider threats are a persistent concern. While external attackers get a lot of attention, employees or former employees with privileged access can also pose a significant risk, whether intentionally or accidentally. PAM helps to lessen this risk by monitoring all privileged activity and making sure that access is revoked when it's no longer needed. This continuous oversight is a key defense against threats from within.
Ultimately, PAM is about reducing risk. By controlling and monitoring who has elevated access, organizations can significantly lower their chances of a data breach, system compromise, or intellectual property theft. It's an information security (infosec) mechanism that safeguards identities with special access or capabilities beyond regular users. This protective layer is a core part of any robust security strategy, making sure that the digital heart of an organization is well-guarded.
PAM in Action: Real-World Impact
When an organization puts Privileged Access Management into practice, the effects are usually quite clear and positive. For example, a large financial institution might use PAM to manage access for its database administrators. Instead of these administrators having permanent, direct access to sensitive customer financial records, PAM could grant them temporary, just-in-time access only when a specific task needs to be done. This means less exposure for critical data.
Consider a scenario where an IT team needs to perform emergency maintenance on a critical server. Without PAM, they might use a shared, highly privileged account, which is a big security risk. With PAM, each team member could be given a unique, temporary credential that expires after the maintenance is complete. Every action they take during that session is logged, providing a full audit trail. This makes it much harder for malicious activity to go unnoticed.
In another instance, a software development company might have developers who need access to production environments for testing or debugging. PAM can ensure that these developers only get access to the specific systems they need, and only for a limited time. This stops them from accidentally or intentionally making changes to unrelated, sensitive systems. It helps maintain a clear separation of duties, which is very important for security.
PAM also plays a big part in incident response. If a security incident occurs, like a suspected breach, the detailed logs provided by PAM can help security teams quickly figure out what happened, who accessed what, and when. This speeds up the investigation and recovery process, reducing the overall impact of the incident. It's like having a security camera that records every single step taken by someone with a master key.
Moreover, PAM helps organizations maintain a stronger security posture over time. By continuously enforcing policies and monitoring privileged activity, it helps to create a culture of security where access is always treated with the seriousness it deserves. It's a system that helps organizations restrict privileged access within an existing and isolated Active Directory environment, making it a flexible and powerful tool for many different types of businesses. This ongoing protection is why PAM is considered so vital.
The Future of PAM: Staying Ahead
Just like any important security solution, Privileged Access Management is always evolving. The digital world doesn't stand still, and neither do the threats. So, the question "is PAM still alive?" is answered by its constant adaptation and growth. We're seeing PAM solutions become even more integrated with other security tools, like identity governance and administration (IGA) and security information and event management (SIEM) systems. This creates a more unified and powerful defense.
One trend we're seeing is the increased use of artificial intelligence (AI) and machine learning (ML) within PAM. These technologies can help detect unusual patterns in privileged activity that human analysts might miss. For example, if an administrator suddenly tries to access a system they've never touched before, or at an odd hour, AI can flag this as suspicious. This proactive detection is a really exciting development.
The move towards "zero trust" security models also means PAM will continue to be a central piece. In a zero-trust model, no user or device is trusted by default, even if they are inside the network. Every access request is verified. PAM fits perfectly into this model by ensuring that even privileged users must constantly prove their identity and justify their access. It's a shift from "trust but verify" to "never trust, always verify," and PAM is key to that.
As organizations increasingly adopt hybrid cloud environments, with some systems on-premises and others in various cloud providers, PAM solutions are adapting to manage privileged access across these diverse landscapes. This means PAM isn't just for your internal network anymore; it's for wherever your data and systems reside. This flexibility ensures that PAM remains relevant and effective in complex IT setups.
Finally, the growing awareness of supply chain attacks means that managing privileged access for third-party vendors and contractors is becoming even more important. PAM solutions are expanding to provide secure, controlled access for these external entities, ensuring that they only have the permissions they need, for the time they need them. This wider scope of protection truly shows that PAM is not only alive but growing in importance.
Frequently Asked Questions About PAM
Is Privileged Access Management (PAM) a new concept?
Actually, the core ideas behind PAM, like controlling access for powerful accounts, have been around for a while in cybersecurity. However, the technologies and strategies for doing this have really grown and become much more sophisticated over time. So, while the concept itself isn't entirely new, its modern implementation and importance are very much current.
Can small businesses benefit from PAM, or is it just for large organizations?
While larger organizations often have more complex needs, small businesses can absolutely benefit from PAM. Even a few privileged accounts in a small company can pose a big risk if not managed properly. There are PAM solutions available that are designed to be scalable and more accessible for smaller teams, helping them protect their critical assets without needing a massive IT budget.
How does PAM differ from regular identity management?
Regular identity management focuses on managing all user accounts and their general access to systems. PAM, on the other hand, specifically focuses on "privileged" accounts, which have elevated permissions that could cause significant damage if misused. It's a specialized branch of identity management that adds a much stronger layer of control and monitoring for those super-powered accounts.
Conclusion: PAM is Very Much Alive
So, to answer the initial question, "is Pam Hardy still alive?" – if we're talking about Privileged Access Management (PAM), the answer is a resounding yes. PAM is not just alive; it's thriving, evolving, and proving itself to be an indispensable part of modern cybersecurity. It stands as a critical defense, tirelessly working to protect an organization’s most sensitive data and critical systems. It’s a cybersecurity strategy and set of technologies aimed at safeguarding these vital assets.
The continued relevance of PAM shows that good security practices are never static; they adapt to new threats and technologies. It's a combination of people, processes, and technology that enables organizations to safeguard their critical assets by enforcing strict controls on who can access privileged information. This ongoing effort to control, monitor, and protect privileged accounts ensures that businesses can operate with greater peace of mind in a world full of digital risks. Learn more about privileged access management on our site, and link to this page understanding PAM's core principles.
What is Privileged Access Management (PAM)? | Delinea

Pam - cháu gái tập đoàn may mặc là em bé Việt đầu tiên có loạt ảnh đạt

Break glass privileged account